OWASP Proactive Controls
OWASP Proactive Controls: Secure Coding ka Ek Must-Have Guide
OWASP Proactive Controls ek security controls ka set hai jo developers ko application development ke har stage par security integrate karne me madad karta hai. Yeh preventive measures hain jo vulnerabilities hone se pehle hi unko mitigate karne me help karte hain, taaki applications secure rahein.
Yeh controls OWASP ka hissa hain, jo software security best practices promote karta hai. Inka purpose hai ki developers sirf functionality par focus na karein, balki security bhi pehle se implement karein, taaki common vulnerabilities jaise SQL Injection, XSS, Authentication flaws, aur misconfigurations ko prevent kiya ja sake.
OWASP Proactive Controls ka Detailed Overview
1. Input Validation 🚦
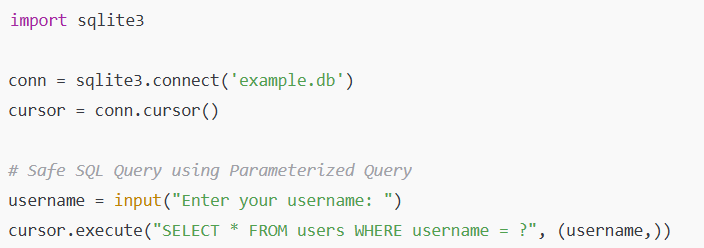
Jab bhi koi bhi input application receive karti hai (user, API, ya kisi aur source se), toh usko validate karna bahut zaroori hota hai. Agar input validation sahi se nahi kiya gaya, toh attackers malicious code inject kar sakte hain, jo security vulnerabilities create karega.
👉 Example:
Agar ek user login form me apna username enter karta hai, lekin instead of normal input, wo SQL query ' OR 1=1 -- enter karta hai, aur agar validation nahi hai, toh SQL injection ho sakta hai.
🛡 Solution:
- Input validation techniques jaise allowlist filtering (whitelisting) aur regular expressions ka use karo.
- SQL Injection rokne ke liye prepared statements aur parameterized queries ka use karo.
2. Output Encoding 🛑
Agar user-generated content ko proper encode nahi kiya gaya, toh wo malicious script execute kar sakta hai, jo Cross-Site Scripting (XSS) attack ka ek bada reason hai.
👉 Example:
Agar ek attacker comment section me yeh JavaScript code daal de:
<script>alert(‘Hacked!’);</script>
Aur agar application isko properly encode nahi karti, toh yeh browser me execute hoga aur XSS attack perform karega.
🛡 Solution:
- HTML entity encoding ka use karo:
<script>ko<script>me convert karo. - Secure libraries jaise OWASP ESAPI ya built-in encoding functions ka use karo.
- HTML entity encoding ka use karo:
3. Authentication 🔑
Authentication ka purpose hai ensure karna ki sirf legitimate users hi system access karein. Weak authentication mechanisms attackers ko credential stuffing ya brute force attacks ka mauka dete hain.
👉 Example:
Agar application weak password policies allow karti hai (jaise 12345 ya password), toh brute force attack se easily account hack ho sakta hai.
🛡 Solution:
- Strong password policies enforce karo (minimum 12 characters, uppercase, lowercase, numbers, symbols).
- Multi-Factor Authentication (MFA) ka use karo.
- Hashing techniques (bcrypt, Argon2) ka use karo taaki passwords secure rahein.
4. Session Management 🕒
Session hijacking ya fixation se bachne ke liye secure session management zaroori hai.
👉 Example:
Agar session ID URL me expose ho rahi hai (https://example.com/home?sessionid=123456), toh koi bhi is session ko reuse kar sakta hai aur user ke session ko hijack kar sakta hai.
🛡 Solution:
- Session ID ko cookies me store karo (URL me nahi).
- Secure, HttpOnly, aur SameSite attributes use karo.
-
- Example
- Set-Cookie: sessionid=xyz123; HttpOnly; Secure; SameSite=Strict
5. Access Control 🚧
Users ko sirf unhi resources ka access dena chahiye jo unke authorization level ke andar ho.
👉 Example:
Agar ek normal user admin panel ka URL manually enter kar ke access kar sake (/admin/dashboard), toh yeh Insecure Direct Object Reference (IDOR) vulnerability hai.
🛡 Solution:
- Role-Based Access Control (RBAC) implement karo.
- Least Privilege principle ka use karo.
return “Access Denied”
6. Secure Communication 🔐
Data ko transit me encrypt karna zaroori hai taaki Man-in-the-Middle (MitM) attacks se bacha ja sake.
👉 Example:
Agar website HTTPS ki jagah HTTP use kar rahi hai, toh attackers network traffic sniff karke sensitive data (passwords, credit card details) chura sakte hain.
🛡 Solution:
- HTTPS (TLS 1.2 ya 1.3) enforce karo
- Secure headers use karo:
Strict-Transport-Security: max-age=31536000; includeSubDomains
7. Error Handling aur Logging 📝
Agar error messages sensitive information leak karte hain, toh yeh attack surface badha sakta hai.
👉 Example:
Agar ek login page me SQL error dikhe:
Error: SQL syntax error near 'admin' at line 1
Toh attacker ko yeh pata chal sakta hai ki backend database SQL queries execute kar raha hai, jo SQL Injection ke chances badha deta hai.
🛡 Solution:
- Generic error messages show karo
- Detailed errors sirf internal logs me store karo
- try:
# Some secure code
except Exception as e:
logging.error(“An error occurred”, exc_info=True)
return “Something went wrong. Please try again.”
8. Data Protection 🔒
Data Protection ek critical aspect hai, jo ensure karta hai ki sensitive data unauthorized access se safe rahe, chahe wo rest (storage) ya transit (network communication) me ho.
🛡 Solution:
Encryption at Rest
- AES (Advanced Encryption Standard) ka use karo, preferably AES-256 jo strongest hai.
- Database me full-disk encryption ya column-level encryption implement karo.
- Cloud storage ke liye KMS (Key Management System) use karo.
Encryption in Transit
- TLS 1.2 ya TLS 1.3 ka use karo HTTPS communication ke liye.
- Secure protocols (e.g., SSH, SFTP, VPN) ka use karo data transfer ke liye.
- Certificate pinning implement karo taaki MITM (Man-in-the-Middle) attacks se bacha ja sake.
Password Storage Best Practices
- Passwords ko plaintext me store mat karo ❌
- Instead, strong hashing algorithms like bcrypt, Argon2, PBKDF2 ka use karo.
- Salting + Hashing implement karo taaki dictionary attacks fail ho jayein.
Tokenization & Masking
- PANs (Payment Account Numbers), Aadhaar, SSN jaise sensitive data ke liye tokenization use karo.
- Masking techniques implement karo jisme sirf last few digits visible ho (e.g., –-1234).
🔥 Bonus Security Tips:
✅ HSTS (HTTP Strict Transport Security) enable karo taaki browsers sirf HTTPS par hi connect karein.
✅ Database access control implement karo taaki sirf authorized users hi sensitive data access kar sakein.
✅ Regular Key Rotation karo taaki encryption keys compromise hone par risk minimize ho.
9. Security Configuration ⚙️
Security Configuration ek important aspect hai jo misconfigurations aur default settings ke weaknesses ko exploit hone se bachata hai. Attackers aksar default configurations ko target karte hain, isliye hardened security settings implement karni chahiye.
🛡 Solution:
1️⃣ Unnecessary Services Disable Karo 🚫
- Unused ports, protocols, and services ko disable karo jo system me required nahi hain.
- Example: Agar FTP, Telnet, RDP use nahi ho raha to disable kar do.
- Linux me:
systemctl disable service-name - Windows me: “Turn Windows Features On or Off” me unnecessary services disable karo
2️⃣ Security Headers Implement Karo 🛑
- Web application ke response headers properly configure karo taaki attacks prevent ho sakein:
X-Frame-Options: DENY # Clickjacking se bachne ke liyeX-Content-Type-Options: nosniff # MIME-type sniffing prevent karta haiContent-Security-Policy: default-src 'self' # XSS aur data injection se bachata haiStrict-Transport-Security: max-age=31536000; includeSubDomains # HTTPS enforce karta haiReferrer-Policy: no-referrer # Sensitive referrer data leak hone se bachaata hai - Apache/Nginx me headers set karne ke liye:
- Apache:
<IfModule mod_headers.c>Header set X-Frame-Options "DENY"Header set X-Content-Type-Options "nosniff"Header set Content-Security-Policy "default-src 'self'"Header set Strict-Transport-Security "max-age=31536000; includeSubDomains"Header set Referrer-Policy "no-referrer"</IfModule> - Nginx:
add_header X-Frame-Options "DENY";add_header X-Content-Type-Options "nosniff";add_header Content-Security-Policy "default-src 'self'";add_header Strict-Transport-Security "max-age=31536000; includeSubDomains";add_header Referrer-Policy "no-referrer";
- Apache:
- Web application ke response headers properly configure karo taaki attacks prevent ho sakein:
3️⃣ Default Credentials Change Karo 🔑
- Admin credentials ko change karo aur strong passwords use karo.
- SSH ke default port 22 ko change karo (e.g.,
Port 2222in/etc/ssh/sshd_config). - WordPress, MySQL, phpMyAdmin ke default logins change karo.
4️⃣ File & Directory Permissions Secure Karo 📂
- Linux/Unix:
chmod 700 sensitive_file # Sirf owner access kar sake chmod 600 private_key.pem # Private key ko secure rakho - Windows: NTFS permissions configure karo taaki unauthorized access na ho.
- Linux/Unix:
5️⃣ Firewall aur IDS/IPS Enable Karo 🔥
- UFW (Uncomplicated Firewall) – Linux ke liye:
sudo ufw enable sudo ufw allow 443/tcp # HTTPS traffic allow karo sudo ufw deny 23 # Telnet disable karo - Windows Defender Firewall ko enable rakho aur unnecessary inbound/outbound rules block karo.
- Intrusion Detection/Prevention System (IDS/IPS) jaise Suricata ya Snort ka use karo.
- UFW (Uncomplicated Firewall) – Linux ke liye:
6️⃣ Logging & Monitoring Enable Karo 📜
- SIEM (Security Information and Event Management) tools like Splunk, ELK Stack use karo.
- Linux me Audit Logs check karo:
sudo cat /var/log/auth.log | grep "failed"
🔥 Bonus Security Tips:
✅ Docker & Kubernetes ke default security configurations harden karo.
✅ Security patches aur updates regularly install karo.
✅ Public cloud services me (AWS, GCP, Azure) security misconfigurations audit karo.
✅ Automated security scanners (e.g., Lynis, OpenVAS, Nikto) se server audit karo.
10. Vulnerability Management 🔍
Vulnerability Management ek continuous process hai jo security flaws ko identify, assess, aur fix karne me madad karta hai. Agar applications aur systems ko regularly scan aur patch na kiya jaye, to attackers unhe exploit kar sakte hain.
🛡 Solution:
1️⃣ Automated Security Scanning Tools Use Karo 🔍
✅ Web Application Security Testing ke liye:
- OWASP ZAP – Automated scanning + Active/Passive testing
- Burp Suite – Web penetration testing + Vulnerability detection
- Nikto – Web server vulnerabilities detect karne ke liye
- Acunetix/Wapiti – Automated web vulnerability scanners
✅ Network & System Vulnerability Scanning ke liye:
- Nmap + NSE Scripts – Network scanning aur misconfigurations detect karne ke liye
- OpenVAS – Open-source vulnerability scanner
- Nessus – Advanced vulnerability scanning + Compliance checks
✅ Code Security Scanning ke liye:
- SonarQube – Static code analysis ke liye
- Snyk/Checkmarx – Dependency vulnerabilities detect karne ke liye
2️⃣ Regular Updates & Security Patches Implement Karo 🔄
✅ OS aur Software Updates:
- Linux:
sudo apt update && sudo apt upgrade -y - Windows: Regular Windows Update enable rakho.
- Linux:
✅ Third-Party Libraries & Dependencies ko Update Karo:
- Python:
pip list --outdated | awk '{print $1}' | xargs -n1 pip install -U - Node.js:
npm outdated && npm update
- Python:
✅ Zero-Day Vulnerabilities ka Track Rakho:
- CVE (Common Vulnerabilities and Exposures) database check karo: https://cve.mitre.org/
- Exploit Database aur Bug Bounty Reports ka review karo.
3️⃣ Penetration Testing & Security Audits Karo 🛠
✅ Manual Pen Testing:
- Web application aur APIs ka manual security testing karo.
- SQL Injection, XSS, IDOR, SSRF jaise vulnerabilities test karo.
✅ Automated & Manual Testing ko Combine Karo:
- CTF challenges ya Bug Bounty scenarios ka practice karo taaki real-world vulnerabilities ka pata chale.
- Security testing ka CI/CD pipelines me integration karo.
🔥 Bonus Security Tips:
✅ Patch Management Strategy implement karo (automated updates + scheduled patching).
✅ Security misconfigurations detect karne ke liye compliance frameworks (CIS Benchmarks, NIST) follow karo.
✅ Logging & SIEM tools (Splunk, ELK, Wazuh) ka use karo taaki vulnerabilities exploit hone se pehle detect ho sake.
