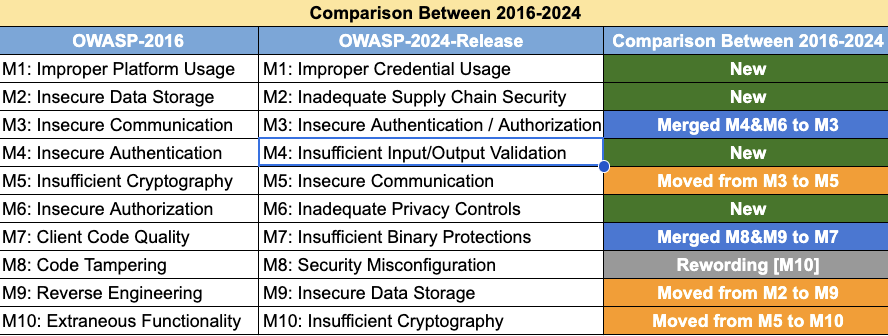
OWASP Mobile Top 10
- M1: Improper Credential Usage
- M2: Inadequate Supply Chain Security
- M3: Insecure Authentication/Authorization
- M4: Insufficient Input/Output Validation
- M5: Insecure Communication
- M6: Inadequate Privacy Controls
- M7: Insufficient Binary Protections
- M8: Security Misconfiguration
- M9: Insecure Data Storage
- M10: Insufficient Cryptography

M1: Improper Credential Usage (Galat Tareeke Se Credentials Ka Use)
* Threat Agents (Hamla Karne Wale Log)
Application Specific (App Ke Anusar)
Agar mobile apps me hardcoded credentials ya improper credential usage ho, toh attackers isko exploit kar sakte hain. Ye attackers automated tools ka use karke hardcoded credentials dhoondh sakte hain ya fir weak credential handling ka fayda utha sakte hain.
* Attack Vectors (Hamla Karne Ke Tarike)
Exploitability: Aasaan (EASY)
Agar app me hardcoded credentials ya improper credential usage ho, toh attackers inhe easily exploit kar sakte hain. Attackers in hardcoded credentials ka use karke sensitive functionalities ka unauthorized access le sakte hain. Agar credentials securely validate ya store nahi hote, toh attackers inka misuse kar sakte hain aur bina permission ke app ya backend systems tak pahunch sakte hain.
* Security Weakness (Suraksha Ki Kamzoriyaan)
Prevalence: Common (Bahut Zyada)
Detectability: Aasaan (EASY)
Agar credentials ka sahi tareeke se management nahi kiya gaya hai, jaise ki hardcoded credentials ka use ya improper handling, toh ye security ke liye bada risk ban sakta hai. Security testers ko testing ke dauraan in issues ko dhoondhna chahiye, jaise ki hardcoded credentials app ke source code ya configuration files me milein.
* Technical Impacts (Takniki Nuksan)
Impact: Bhayankar (SEVERE)
Agar credentials ko sahi tareeke se manage nahi kiya gaya, toh unauthorized users sensitive information ya functionality tak pahunch sakte hain. Isse data breach, user privacy loss, fraud, aur even admin functionalities ka access bhi mil sakta hai.
* Business Impacts (Vyapaar Par Asar)
Impact: Bhayankar (SEVERE)
Agar credentials sahi tareeke se manage nahi kiye gaye, toh business ko nuksan ho sakta hai, jaise:
- Reputation kharab hona (Brand ki chhavi bigad sakti hai)
- Information chori (Data theft)
- Fraud hone ka khatra
- Unauthorized data access
* Kya Aapki App "Improper Credential Usage" Se Affected Hai ?
Agar mobile app insecure credential management use karti hai, toh ye vulnerabilities ho sakti hain:
✅ Hardcoded Credentials – Agar app ke source code ya config files me hardcoded credentials milein, toh ye vulnerability hai.
✅ Insecure Credential Transmission – Agar credentials bina encryption ke bheje ja rahe hain ya insecure channels ka use ho raha hai, toh ye issue hai.
✅ Insecure Credential Storage – Agar credentials device me insecure tareeke se store ho rahe hain, toh ye vulnerability ho sakti hai.
✅ Weak User Authentication – Agar authentication weak hai ya easily bypass ho sakta hai, toh attackers iska fayda utha sakte hain.
* "Improper Credential Usage" Ko Kaise Rokein ?
Agar aapko credentials securely manage karne hain, toh ye steps follow karein:
✅ Hardcoded Credentials Mat Use Karo
Hardcoded credentials attackers ke liye asaan target hote hain. App ke source code ya configuration files me hardcoded credentials na rakhein.
✅ User Credentials Ko Properly Handle Karein
- Credentials ko encrypt karein jab unka transmission ho raha ho.
- User credentials ko device pe store mat karein; secure access tokens ka use karein.
- Strong authentication protocols implement karein.
- API keys ya tokens ko regular update aur rotate karein.
* Example Attack Scenarios
Scenario #1: Hardcoded Credentials
Ek attacker app ke source code me hardcoded credentials dhoondh leta hai aur unka use karke sensitive functionality ya backend systems ka unauthorized access le leta hai.
Scenario #2: Insecure Credential Transmission
Agar app credentials ko bina encryption ke bhejti hai, toh attacker inhe intercept karke ek legitimate user ki tarah access le sakta hai.
Scenario #3: Insecure Credential Storage
Agar ek attacker kisi device ka physical access le leta hai aur app ke insecure stored credentials ko extract kar leta hai, toh wo user account ka unauthorized access le sakta hai.
M2: Inadequate Supply Chain Security | Mobile App Security Risks
* Kya Hai Supply Chain Attack ?
Agar kisi mobile application ke development process me security ka dhyan nahi rakha jaye, to attacker usme malicious code, spyware ya backdoor inject kar sakta hai. Isse data breach, unauthorized access, ya device compromise ho sakta hai. Attackers third-party SDKs, APIs, libraries aur insecure app signing ka bhi misuse kar sakte hain.
* Attack Vectors ( Kaise Attack Ho Sakta Hai ? )
- Malware Injection – Development phase me malicious code inject kiya jata hai jo user ke sensitive data ko chura sakta hai.
- Third-Party Library Exploit – Vulnerable ya outdated libraries ka istemal karne se attacker exploit kar sakta hai.
- Weak App Signing – Attackers fake certificates ka use karke malware ko as a legitimate app distribute kar sakte hain.
- Insecure API Usage – Third-party APIs agar properly secured nahi hain to attacker inhe compromise kar sakta hai.
* Security Weaknesses ( Kamiyaan Jo Attack Ko Asaan Banati Hain )
- Secure coding practices ka na hona.
- Weak code review aur insufficient testing.
- Unverified third-party components ka use.
- Weak encryption aur data security policies ka na hona.
- App update aur patching process me security ka dhyan na dena.
* Technical Impacts ( Cyber Attack Se Kya Nuksaan Ho Sakta Hai ? )
- Data Breach – Attackers login credentials, financial data, aur personal information chura sakte hain.
- Malware Infection – Attacker malicious code inject karke spyware ya ransomware distribute kar sakta hai.
- Unauthorized Access – Attackers admin privileges le kar data modify ya delete kar sakte hain.
- System Compromise – App ya server ka pura control hacker ke haath me aa sakta hai.
* Business Impacts ( Company Ko Kya Nuksaan Ho Sakta Hai ? )
- Financial Losses – Data breach ke baad legal penalties, customer compensation aur revenue loss ho sakta hai.
- Reputational Damage – User trust loss hone se app ka market value gir sakta hai.
- Legal Consequences – GDPR, HIPAA, IT Act jaise cyber laws ke violations pe heavy fines lag sakte hain.
- Supply Chain Disruption – Attack ke wajah se services downtime aur business loss ho sakta hai.
* Aap Vulnerable Hai Ya Nahi ?
Agar aap kisi third-party developer ke apps use kar rahe hain, outdated libraries ka use ho raha hai, ya aapka testing aur security awareness weak hai, to aap vulnerable ho sakte hain.
* Prevention ( Cyber Attack Se Bachne Ke Tarike )
✔ Secure coding practices ka use karein aur regular penetration testing karayein.
✔ Trusted third-party libraries aur verified APIs ka hi use karein.
✔ App signing aur distribution process ko properly secure karein.
✔ Supply chain monitoring aur real-time threat detection ka system implement karein.
✔ Regular security audits aur vulnerability assessments conduct karein.
* Example Attack Scenario – Malware Injection
Ek hacker ek popular mobile app ke code me malware inject karta hai. Uske baad attacker fake certificates ka use karke app store pe upload karta hai. Users jab is app ko install karte hain, to malware login credentials aur personal data chura leta hai. Is data ka use identity theft aur financial fraud me kiya jata hai.
M3: Insecure Authentication/Authorization
Threat Agents
📌 Application Specific
Authentication aur authorization vulnerabilities ka exploitation karne wale threat agents automated attacks ka use karte hain, jo ya toh available tools hote hain ya custom-built hote hain.
Attack Vectors
🚨 Exploitability: EASY
Jab attacker authentication ya authorization vulnerabilities samajh leta hai, toh do tareekon se exploit kar sakta hai:
- Fake/Bypass Authentication – Mobile app ko bypass karke direct backend server ko service request bhej kar authentication ka process tod sakta hai.
- Privilege Escalation – Ek valid user ke roop mein login karne ke baad kisi vulnerable endpoint par force-browsing karke admin functionality ko execute kar sakta hai.
Yeh exploitation zyada tar mobile malware ya botnets ke through kiya jata hai.
Security Weakness
🔍 Prevalence: COMMON 🕵️♂️ Detectability: AVERAGE
Mobile apps me authorization aur authentication vulnerabilities detect karne ke liye penetration testers kaafi strategies use karte hain:
-
- Binary Attacks – Offline mode me privileged functionality execute karne ki koshish.
- Session Token Manipulation – Kam-privilege wale token se admin-level POST/GET requests execute karne ka attempt.
- Offline Authentication Bypass – Offline mode me authentication ko bypass karke functionality access karne ki koshish.
- Anonymous API Execution – Session token hata kar backend API request execute karne ka test.
💡 Common Problems :
- Short passwords ya 4-digit PINs ka use
- Offline authentication ka improper implementation
- Mobile device par authorization decisions lena instead of remote server
Technical Impacts
- Privilege Escalation – Attacker unauthorized admin actions execute kar sakta hai.
- Audit Failure – Authentication fail hone par logs/audit ka loss ho sakta hai, jisse attack detect karna mushkil ho jata hai.
- Anonymous Code Execution – Agar attacker bina authentication ke code execute kar raha hai toh authorization controls bhi weak hain.
Business Impacts
⚠️ Impact: SEVERE
- 🚨 Reputation Damage
- 📂 Information Theft
- 💰 Fraud
- 🔓 Unauthorized Access to Data
Am I Vulnerable To ‘Insecure Authentication / Authorization’?
Authentication aur authorization me farq samajhna zaroori hai:
✅ Authentication – User ki identity verify karta hai.
✅ Authorization – Verify karta hai ki user ke paas requested action perform karne ka permission hai ya nahi.
🔴 Insecure Authorization Indicators:
- IDOR Vulnerabilities – Authorization check nahi ho raha.
- Hidden Endpoints – Backend par authorization missing hai.
- User Role Transmission – Mobile app ke request me user ka role bhejna.
🔴 Insecure Authentication Indicators:
- Anonymous API Execution – Backend API bina access token ke chal raha hai.
- Local Storage of Passwords – App device me passwords ya secrets store kar rahi hai.
- Weak Password Policy – Short ya predictable passwords ka use.
- Biometric Authentication Dependence – FaceID ya TouchID ka improper use.
How To Prevent ‘Insecure Authentication & Authorization ?
🚫 Avoid Weak Authentication Patterns:
✅ Mobile app ke authentication rules web app se kam secure nahi hone chahiye.
✅ Local authentication risky hoti hai – Jailbroken devices par bypass ho sakti hai.
✅ Authentication ko server-side implement karo.
✅ Remember Me feature me passwords kabhi bhi device me store nahi hone chahiye.
✅ 4-digit PINs avoid karo – Strong password policies implement karo.
🔒 Reinforce Authentication:
✅ Assume karo ki client-side authorization bypass ho sakta hai.
✅ Server-side verification karo – Mobile device ke authorization pe depend mat karo.
✅ Local integrity checks implement karo – Binary attacks detect karne ke liye.
✅ FaceID/TouhID ko sirf secrets unlock karne ke liye use karo, authentication ke liye nahi.
🛡️ Prevent Insecure Authorization:
✅ Backend server independently user roles verify kare.
✅ Client-side authorization bypass ho sakti hai – Server-side controls implement karo.
✅ Offline authorization checks me local integrity verification use karo.
Example Attack Scenarios
⚠️ Scenario #1: Hidden Service Requests
- Backend request ko user authentication se link nahi karta.
- Attacker backend ko directly request bhej kar functionality execute kar leta hai.
⚠️ Scenario #2: Interface Reliance
- Devs assume karte hain ki sirf authorized users specific features dekhenge.
- Backend request ke identity verification ke bina execute hone ki wajah se low-privilege accounts bhi admin actions perform kar sakte hain.
⚠️ Scenario #3: Weak Password Policy
- 4-digit PINs ka use hone ki wajah se rainbow hash tables se passwords crack ho sakte hain.
⚠️ Scenario #4: Insecure Direct Object Reference (IDOR)
- API request me actor ID aur bearer token send kiya jata hai.
- Backend actor ID verify nahi karta, jisse attacker kisi aur user ka data access kar sakta hai.
⚠️ Scenario #5: LDAP Role Transmission Manipulation
- Backend oAuth bearer token verify karta hai, lekin LDAP group membership independently verify nahi karta.
- Attacker LDAP group modify karke admin access le sakta hai.
M4: Insufficient Input/Output Validation
Threat Agents - Insufficient Input/Output Validation 🔥
Application-Specific Risk
Jab koi mobile application user input ya network data ko properly validate aur sanitize nahi karti, toh yeh severe security vulnerabilities introduce kar sakti hai. Mobile-specific attacks jaise:
✅ SQL Injection (Malicious SQL Queries)
✅ Command Injection (System Commands ka Unauthorized Execution)
✅ Cross-Site Scripting (XSS) (Malicious JavaScript Injection)
⚠️ Possible Risks:
🚨 Unauthorized Access – Sensitive user data (passwords, personal info) leak ho sakta hai.
🚨 App Function Manipulation – Attacker app ke features ko exploit kar sakta hai.
🚨 Mobile System Compromise – Poor validation se pura device ya backend system control hone ka risk hota hai.
📌 Output Validation Bhi Important Hai!
Agar output validation nahi hoti, toh:
❌ Data corruption ho sakta hai.
❌ Attackers malicious scripts inject karke UI ya user data manipulate kar sakte hain.
❌ Users ko fake content ya phishing attacks ka shikar banaya ja sakta hai.
💡 Conclusion: Mobile applications me input aur output validation ek must-have security practice hai jo security vulnerabilities se bachne ke liye zaroori hai. 🚀
Attack Vectors - Insufficient Input/Output Validation 🚨
🔴 Exploitability: 🚧 Difficult (Par possible hai!)
🔴 Prevalence: ⚠️ Common (Bohot zyada dekha jata hai!)
🔴 Detectability: 🔍 Easy (Attackers asani se exploit kar sakte hain!)

📌 Key Attack Vectors
✅ SQL Injection – Malicious SQL queries dal ke database access karna.
✅ Cross-Site Scripting (XSS) – Malicious scripts inject karke user sessions ya sensitive data churana.
✅ Command Injection – System ke commands execute karke unauthorized access lena.
✅ Path Traversal – Restricted files ya directories ka unauthorized access lena.
Common Exploits & Their Risks ⚠️
🔹 1. Insufficient Input Validation
- Attacker unexpected/malicious input de sakta hai jo security ko bypass karke code execution ya unauthorized access kar sakta hai.
- Example: ‘ OR 1=1 — (SQL Injection)
🔹 2. Insufficient Output Validation
- Agar output sanitize nahi hui toh malicious scripts execute ho sakte hain.
- Example: XSS attacks, jisme attacker user ke browser me malicious JavaScript inject kar sakta hai.
🔹 3. Lack of Contextual Validation
- Har data ka context samajhna zaroori hai. Agar wrong validation hui toh SQL Injection, Format String vulnerabilities ho sakti hain.
- Example: Agar database query bina sanitization ke
user_inputaccept kare toh attacker queries manipulate kar sakta hai.
🔹 4. Failure to Validate Data Integrity
- Attackers critical system variables modify kar sakte hain ya malformed data bhej ke app ka function disrupt kar sakte hain.
Why Do These Vulnerabilities Exist ?🎯
❌ Poor application logic – Developers validation ka dhyan nahi dete.
❌ Incomplete validation checks – Har input ko sanitize aur validate nahi kiya jata.
❌ Lack of security awareness – Developers secure coding practices follow nahi karte.
❌ Insufficient testing & code reviews – Security vulnerabilities identify nahi ho pati.
💡 Conclusion: Proper input validation, output sanitization, and security testing se hi in vulnerabilities se bach sakte hain! 🚀
Technical Impacts
1. Code Execution⚠️
Impact: 🚨 SEVERE (Bohot hi nuksaan pohcha sakta hai ! )
SEVERE (Bahut zyada critical)
Agar input/output validation sahi se nahi hoti, toh yeh vulnerabilities bahut bade technical risks bana sakti hain. Chaliye inko detail mein dekhte hain:
- Malicious actors is vulnerability ka fayda utha ke unauthorized code execute kar sakte hain.
- Agar input/output validation sahi se nahi hui, toh attacker malicious code ko application environment me execute kar sakta hai.
- Bypass Security Measures: Attackers system ke internal commands run karke sensitive operations perform kar sakte hain.
- Result: Security measures bypass hote hain aur unauthorized code execute hota hai.
- Example: Web application me command injection se server control karna.
- DROP TABLE users; —
- Agar input validate nahi hui, toh yeh command pura user database delete kar sakta hai.
2. Data Breaches ⚠️
- Malicious inputs ke through attackers sensitive data ko access aur exfiltrate kar sakte hain.
- Insufficient validation se attackers input manipulate karke unauthorized data access le sakte hain.
- Sensitive Information Leak: Users ke passwords, financial data, ya personal information expose ho sakti hai.
- SQL Injection se user credentials churana.
- Example: SQL Injection ke through attacker entire user data extract kar sakta hai.
- SELECT * FROM users WHERE username = ‘admin’ — AND password = ”;
3. System Compromise 🖥️
- Attackers bina authorization ke kisi system tak pahunch kar usko compromise kar sakte hain, jisse data chori, malware injection aur system control ka risk badh jata hai
- Attackers operating system ya server resources par unauthorized access le sakte hain, jo system ke security ko compromise kar sakta hai.
- 🛑 Example: Command Injection Attack
Agar koi system properly secured nahi hai, to ek attacker command injection se root privileges le sakta hai.
cat /etc/passwd
- 👆 Yeh command Linux system par users ke details nikalne ke liye use hoti hai. Agar system vulnerable hai, to attacker password hashes extract karke system ka control le sakta hai. 😨
🔐 Bachav kaise karein?
- Input sanitization implement karo
- Least privilege principle follow karo
- WAF (Web Application Firewall) use karo
- Regular security audits aur patching karo
Security best practices follow karna must hai warna aise attacks hone ka chance badhta hai! 🚨
4. Application Disruption💥⚠️
⚠️ Malicious Input ka Impact: App Crash, Data Corruption aur Downtime.
Attackers malicious input ka istemal karke applications ko crash, data corrupt ya unreliable bana sakte hain. Yeh security aur performance dono ke liye dangerous hai! 😨
🔴 Result:
- Downtime badh jata hai
- Users ko service disruptions ka samna karna padta hai
- Data corruption ya loss ho sakta hai
💥 Example 1: Buffer Overflow Attack
Agar application input size validate nahi karti, to attacker extra data inject karke app ko crash kar sakta hai.
💥 Example 2: Invalid JSON Input
Agar application data type validation na kare, to yeh errors aur instability cause kar sakta hai:
{
"username": "admin",
"age": "twenty-five" // "age" field integer hona chahiye
}
👆 Yeh input system ko confuse kar sakta hai, jis se errors ya crashes ho sakte hain.
🔐 Prevention Tips:
✅ Input validation implement karo (e.g., regex, type checking)
✅ Proper error handling karo taaki app crash na ho
✅ Memory safe programming practices follow karo (Buffer Overflow prevent karne ke liye)
✅ Secure coding principles adopt karo
Application ki reliability aur security dono zaroori hai! Malicious inputs ka sahi tareeke se handling na hui to users ko frequent errors aur downtime ka samna karna pad sakta hai. 🚨
5. Reputation Damage 📉⚠️
Data Breach ka Asar: Customer Trust & Business Reputation Ka Risk🔴
Ek data breach sirf technical problem nahi hai, balki yeh customer trust ko bhi damage karta hai, jo business ke liye long-term loss cause kar sakta hai. 🚨
💥 Result:
- Reputation damage – Customers ka bharosa toot sakta hai
- Brand image pe negative impact padta hai
- Financial loss – Customers aur investors ka confidence gir jata hai
🔴 Example:
Agar ek company ka customer data leak ho jaye, to:
- News & media me negative coverage aati hai
- Customers service par trust lose kar dete hain
- Social media pe negative reviews aur complaints badhne lagte hain
- Business competitors ka advantage badh jata hai
💔 Successful exploitation ka direct impact:
✅ Customers apni services cancel kar sakte hain
✅ Business ko legal penalties ka samna karna pad sakta hai
✅ Market value aur share prices gir sakti hain
🔐 Prevention Tips:
🔹 Data encryption implement karo taaki sensitive information secure rahe
🔹 Regular security audits aur penetration testing karo
🔹 Multi-factor authentication (MFA) implement karo
🔹 Employees ko cybersecurity best practices sikhayo
⚠️ Customer trust ek baar kharab ho gaya to wapas jeetna mushkil hota hai! Isliye proactive security measures lena business ke liye must hai. 🚀
6. Legal and Compliance Issues ⚖️⚠️
Insufficient Validation = Data Protection Laws ka Violation ⚠️
Agar proper data validation nahi hoti, to yeh data protection laws ka violation kar sakti hai, jo legal penalties aur compliance issues cause karta hai. 🚨
💥 Result:
- Heavy regulatory fines aur legal actions
- Compliance audits aur lawsuits ka risk
- Business reputation aur financial loss
🔴 Example:
Agar koi company GDPR (General Data Protection Regulation) ya CCPA (California Consumer Privacy Act) ka violation karti hai, to:
✅ Multi-million dollar fines lag sakti hain
✅ Legal lawsuits face karne pad sakte hain
✅ Regulatory authorities audits aur bans laga sakti hain
💰 Regulatory Penalties ke Examples:
🔹 2021 me Amazon ko $877 million ka GDPR fine laga tha 🚨
🔹 Meta (Facebook) ko $1.3 billion ka fine mila GDPR violation ke liye
🔹 Equifax ka data breach hua to $700 million settlement dena pada
🔐 Prevention Tips:
✔️ Strong data validation aur security measures implement karo
✔️ Regulatory compliance check karo (GDPR, CCPA, DPA, etc.)
✔️ Regular security audits aur penetration testing karo
✔️ Customer data encryption aur access control implement karo
⚠️ Compliance ignore karna sirf financial nahi, balki business survival ke liye bhi risk hai! Proactive security best practices zaroori hain. 🚀
Business Impacts
Insufficient input/output validation ek serious vulnerability hai jo technical aur business dono aspects ko affect karti hai.
⚙️ Technical Impacts:
🚨 Code Execution: Attackers unauthorized code execute kar sakte hain, jisse system compromise aur unauthorized access ho sakta hai.
🔓 Data Breaches: Insufficient validation ka use karke attackers input manipulate kar sakte hain, jisse sensitive data leak ho sakta hai.
⚠️ System Disruptions: Yeh vulnerability app crash, instability ya data corruption ka reason ban sakti hai, jisse service disruptions aur operational issues ho sakte hain.
📉 Data Integrity Issues: Agar validation proper nahi hai, to data corruption, incorrect processing aur inaccurate outputs ho sakte hain, jo system ki reliability aur integrity ko compromise kar sakte hain.
💼 Business Impacts:
🔴 Reputation Damage: Agar vulnerability exploit ho gayi, to data breaches, system failures aur customer distrust badh sakta hai, jo brand image aur reputation ko bigaad sakta hai.
⚖️ Legal & Compliance Issues: Data protection laws (GDPR, CCPA, etc.) ka violation hone par legal action, heavy fines aur compliance penalties face karni pad sakti hain.
💰 Financial Losses: Data breaches aur service disruptions hone par incident response, remediation, legal fees aur revenue loss ho sakta hai, jo business ke liye long-term financial impact create karega.
🛑 Prevention best practices follow karna zaroori hai, warna business ko serious risks face karne pad sakte hain! 🚨
Kya Aap ‘Insufficient Input/Output Validation’ ke Vulnerable Hain ?🔍
Agar ek application proper input/output validation implement nahi karti, to yeh multiple security risks create kar sakti hai. Yeh vulnerabilities kaafi common hain aur attackers inse system compromise ya data breaches execute kar sakte hain.
❌ Vulnerable Hone Ke Reasons:
⚠️ Lack of Input Validation: Agar user input properly validate nahi hota, to SQL Injection, Command Injection, ya XSS jaise attacks ho sakte hain.
⚠️ Inadequate Output Sanitization: Agar output data sanitize nahi hota, to XSS attacks ka risk badhta hai, jisme attackers malicious scripts inject karke users ka control le sakte hain.
⚠️ Context-Specific Validation Neglect: Data context ke according validation apply nahi karna Path Traversal, Unauthorized File Access jaise attacks ka chance badhata hai.
⚠️ Insufficient Data Integrity Checks: Agar proper integrity checks nahi hain, to data corruption ya unauthorized modifications ka risk hota hai, jo system ki security aur reliability ko compromise kar sakta hai.
⚠️ Poor Secure Coding Practices: Agar secure coding guidelines follow nahi hoti (e.g., parameterized queries, escaping, ya encoding techniques ka use nahi hota), to yeh vulnerabilities create kar sakta hai.
✅ ‘Insufficient Input/Output Validation’ Se Kaise Bachein?
🔹 Input Validation:
✔️ Strict validation techniques use karo taaki malicious input reject ho sake
✔️ Input length restrictions implement karo aur unexpected ya harmful data reject karo
🔹 Output Sanitization:
✔️ Output data ko properly sanitize karo taaki XSS attacks prevent ho sake
✔️ Data display ya transmission ke waqt output encoding techniques ka use karo
🔹 Context-Specific Validation:
✔️ Context-based validation apply karo (e.g., file uploads, DB queries) taaki Path Traversal aur Injection Attacks prevent ho sake
🔹 Data Integrity Checks:
✔️ Data integrity ko maintain karne ke liye hashing, checksums, aur cryptographic techniques ka use karo
🔹 Secure Coding Practices:
✔️ Parameterized queries aur prepared statements use karo taaki SQL Injection prevent ho sake
✔️ Secure coding guidelines follow karo taaki validation loopholes na bane
🔹 Regular Security Testing:
✔️ Penetration testing aur code reviews conduct karo taaki vulnerabilities detect aur fix ki ja sakein
⚠️ Security best practices implement karna zaroori hai warna attackers inhi chhoti chhoti vulnerabilities ka fayda uthakar system compromise kar sakte hain! 🚨
Yeh vulnerabilities applications aur devices ke liye high-risk threats create karti hain. Niche kuch real-world attack scenarios diye gaye hain jo is risk ko samjhane me madad karenge.
⚡ Scenario #1 – Remote Code Execution via Malicious Input
🔴 Attack Flow:
1️⃣ Attacker ek mobile application identify karta hai jisme proper input validation aur sanitization nahi hai.
2️⃣ Malicious input craft karke unexpected characters inject karta hai.
3️⃣ Due to insufficient validation, application input ko mishandle karti hai aur vulnerability expose ho jati hai.
4️⃣ Attacker arbitrary code execute kar leta hai, jisse device resources aur sensitive data ka access mil jata hai.
💥 Impact: Attacker unauthorized access le sakta hai aur device ko compromise kar sakta hai.
⚡ Scenario #2 – Injection Attacks via Insufficient Output Validation
🔴 Attack Flow:
1️⃣ Attacker ek mobile app identify karta hai jo output validation aur sanitization properly implement nahi karti.
2️⃣ User-generated content ya untrusted data ko process karne wale input points exploit karta hai.
3️⃣ Malicious input craft karta hai jo code ya script injections contain karta hai (e.g., HTML, JavaScript, SQL).
4️⃣ Application crafted input ko validate ya sanitize nahi karti, jis wajah se injected code execute ho jata hai.
5️⃣ Attacker XSS ya SQL Injection jese attacks perform karke application ka control le sakta hai.
💥 Impact: Application compromise ho sakti hai, sensitive information leak ho sakti hai, aur users ko phishing ya session hijacking ka risk ho sakta hai.
⚡ Scenario #3 – Remote Code Execution via Malformed Output
🔴 Attack Flow:
1️⃣ Attacker ek mobile application identify karta hai jo user-provided data ko process karke dynamic output generate karti hai.
2️⃣ Attacker specially formatted malicious data craft karta hai taaki application ke insufficient output validation ka fayda uthaya ja sake.
3️⃣ Attacker yeh malformed data ya to directly submit karta hai ya kisi exposed API ke through inject karta hai.
4️⃣ Application properly output sanitize nahi karti, jisse attacker ka crafted data execute ho jata hai ya unintended actions trigger hote hain.
5️⃣ Attacker remote code execution achieve karta hai aur mobile device, uske resources ya sensitive data ka full control le leta hai.
💥 Impact: Device fully compromised ho sakta hai, aur sensitive information attacker ke control me aa sakti hai.
🔐 Prevention Tips:
✅ Input validation aur sanitization properly implement karo
✅ Output encoding aur escaping techniques ka use karo
✅ Secure coding practices adopt karo (parameterized queries, prepared statements, etc.)
✅ Regular penetration testing aur security audits conduct karo
⚠️ Agar input/output validation weak hai to attackers easily system compromise kar sakte hain! Proactive security best practices follow karna zaroori hai! 🚀
M5: Insecure Communication
🛡️ Threat Agents – Application Specific

Aaj kal ke modern mobile applications aksar data exchange karte hain ek ya zyada remote servers ke saath. Jab yeh data transmission hota hai, to yeh usually mobile device’s carrier network aur internet se guzarta hai. Agar data plaintext ya deprecated encryption protocol ke saath transmit hota hai, to koi threat agent jo network par listen kar raha ho, woh is data ko intercept aur modify kar sakta hai. Yeh threat agents alag-alag motives ke saath attack karte hain, jaise ki sensitive information churaana, espionage, identity theft, etc. Kuch common threat agents hain:
- Local network adversary (compromised ya monitored Wi-Fi).
- Rogue carriers ya network devices (routers, cell towers, proxy, etc).
- Malware jo aapke mobile device par installed ho.
Attack Vectors – Exploitability ⚔️
EXPOSURE: EASY
Aaj kal ke apps SSL/TLS jaise cryptographic protocols use karte hain taaki data securely transfer ho sake. Lekin kabhi-kabhi in protocols mein kuch flaws hote hain, jo attack vectors ban jaate hain:
Deprecated Protocols ya Bad Configuration Settings:
- Example: Agar app purani SSL/TLS versions use kar raha ho ya weak cipher suites use ho rahe ho, toh attacker POODLE jaise attacks se data ko decrypt kar sakte hain.
Bad SSL Certificates Ko Accept Karna:
- Example: Agar app self-signed, expired ya mismatched SSL certificates ko bina validate kiye accept kar raha ho, toh attacker man-in-the-middle attack kar sakte hain, jisme wo malicious server se connect ho jaate hain aur sensitive data intercept kar lete hain.
Inconsistent SSL/TLS Usage:
- Example: Agar app sirf kuch specific workflows (jaise authentication) ke liye SSL/TLS use kar raha ho aur baaki workflows (jaise data transmission) ke liye nahi, toh attacker unprotected channels ko exploit karke sensitive information ko intercept kar sakte hain.
Mitigation Strategies:
- Updated and Strong Protocols Use Karna: App ko hamesha latest versions aur strong cipher suites ke saath configure karna chahiye taaki known vulnerabilities se bacha jaa sake.
- SSL Certificates Ko Properly Validate Karna: App ko strictly validate karna chahiye SSL certificates ko taaki invalid ya compromised certificates ko accept na kiya jaaye.
- Consistent Encryption Apply Karna: App mein har ek data transmission channel par SSL/TLS encryption apply karna chahiye, taaki sensitive information har waqt protect ho sake.
Agar yeh vulnerabilities address kar liye jaaye, toh mobile apps ko common attack vectors se kaafi had tak protect kiya jaa sakta hai.
🔐 Security Weakness – Prevalence
COMMON | Detectability: AVERAGE
Aaj kal ke modern apps apne network traffic ko secure karne ki koshish karte hain, lekin kabhi-kabhi unme kuch implementation flaws hote hain, jo sensitive data aur session IDs ko intercept karne ka risk bana dete hain. Yeh zaroori nahi ki bas app SSL/TLS use karne se secure ho, agar uska implementation galat ho.
Example:
Agar app ne SSL/TLS to implement kiya ho, lekin session ID ko HTTP request me plain text mein bheja jaa raha ho, toh attacker easily session hijacking kar sakta hai.
Detectability:
Basic flaws ko identify karna relatively simple hai. Aap network traffic ko observe karke dekhein toh easily identify kiya jaa sakta hai agar traffic unencrypted hai ya SSL/TLS mein flaws hain. Lekin subtle flaws jaise improper session handling ya weak cryptographic settings ko detect karne ke liye aapko app ke design aur configuration ka deep analysis karna padta hai.
Mitigation:
- Correct SSL/TLS Implementation: Ensure karo ki SSL/TLS properly implement ho aur har sensitive data ko encrypt kiya jaa raha ho.
- Session Management: Session IDs ko hamesha securely transmit karo aur unhe session hijacking se protect karne ke liye proper techniques use karo.
Agar in flaws ko identify karke fix kar liya jaaye, toh app ki security significantly improve ho sakti hai.
Technical Impacts – Impact
SEVERE
Yeh flaw user data ko expose kar sakta hai, jo aage chal ke account takeover, user impersonation, aur PII (Personally Identifiable Information) data leaks tak lead kar sakta hai.
Example:
Agar attacker network traffic ko intercept kar leta hai, toh wo user ke credentials, session IDs, ya 2FA tokens capture kar sakta hai. Isse attacker ko user ke account ko hijack karne ka access mil sakta hai, jo baad mein advanced attacks jaise phishing, data theft, ya fraud ko enable kar sakta hai.
Impact:
- Account Takeover: Attacker user ke account ko control kar sakta hai aur unauthorized actions perform kar sakta hai.
- User Impersonation: Attacker user ki identity ko impersonate kar sakta hai, jisse trust breach ho sakta hai aur system ke integrity ko compromise kiya jaa sakta hai.
- PII Data Leaks: Sensitive personal information jaise address, phone number, aur financial details leak ho sakti hain, jo serious privacy violations aur legal issues ko lead kar sakti hai.
Mitigation:
- Encryption: SSL/TLS jaise strong cryptographic protocols ko ensure karo taaki sensitive data securely transmit ho sake.
- Secure Session Management: Session IDs aur authentication tokens ko securely store aur transmit karo, aur proper session expiry mechanisms implement karo.
- 2FA Implementation: 2FA ko properly implement karo taaki user authentication aur access ko extra layer of security mil sake.
Business Impacts – Impact 💼
MODERATE
Agar sensitive data intercept ho jaata hai, toh privacy violation ho sakta hai. Isse user confidentiality violate hoti hai, jo identity theft, fraud, ya reputational damage ka reason ban sakti hai.
Example:
Agar attacker user ke sensitive data jaise passwords, session tokens, ya personal info ko intercept kar leta hai, toh wo user ke account ko access kar sakta hai aur unke naam pe fraud actions kar sakta hai. Isse business ka trust aur reputation damage ho sakta hai.
📡 Am I Vulnerable To ‘Insecure Communication’?
Yeh risk mobile-to-mobile, app-to-server, ya mobile-to-other communications ko cover karta hai. Isme TCP/IP, WiFi, Bluetooth/Bluetooth-LE, NFC, audio, infrared, GSM, 3G, SMS etc. aati hain.
Sensitive data jaise encryption keys, passwords, user info, aur session tokens ko transmit karte waqt agar communication insecure ho, toh data integrity, confidentiality, aur origin integrity risk mein aa jaati hai.
Example:
Agar sensitive data WiFi ya Bluetooth jaise unsecured channels par transmit ho raha ho, toh attacker us data ko intercept kar sakta hai aur integrity violate ho sakti hai.
Insecure Data: Agar data locally stored ho aur encrypt na kiya ho, toh woh easily compromised ho sakta hai.
Insecure Authentication: Agar session identifier weak ya predictable ho, toh attacker easily session hijacking ya brute force attacks kar sakta hai.
Mitigation:
- Secure Communication Protocols: Use karo SSL/TLS jaise secure communication protocols ko taaki data transmit karte waqt uska integrity aur confidentiality maintain rahe.
- Data Encryption: Sensitive data ko securely store aur encrypt karo taaki agar data compromise ho, toh wo useless ho.
- Strong Session Identifiers: Session tokens ko strong, random aur unpredictable banaao taaki session hijacking ka risk kam ho.
🛡️ How Do I Prevent ‘Insecure Communication’?
General Best Practices:
Network Layer Ko Insecure Samjho:
Network layer ko hamesha insecure samajh ke usme sensitive data transmit na karo. Data ko kabhi bhi plaintext mein transmit mat karo, chahe woh local network ho ya public internet.SSL/TLS Ka Use Karna:
Jab app backend API ya web service se data transmit kar rahi ho, hamesha SSL/TLS ka use karo taaki data encrypted rahe aur secure transmission ho.Strong Cipher Suites Use Karna:
Strong aur modern cipher suites ko use karo aur trusted CA (Certificate Authority) certificates se certificates ko verify karo taaki data ki integrity aur confidentiality maintain ho.Bad Certificates Ko Kabhi Allow Mat Karna:
Kabhi bhi bad certificates (jaise self-signed, expired, ya revoked certificates) ko allow mat karo. Certificate pinning ko consider karo, taaki aap sirf trusted certificates ko accept kar sakein.Secure Connection Establish Karna:
Hamesha secure connection establish karo jab server ki identity ko trusted certificate ke through verify kiya ho.Sensitive Data Ko Alternate Channels Se Mat Send Karo:
Sensitive data ko kabhi bhi SMS, MMS, ya notifications ke through send na karo, kyunki yeh insecure channels hote hain.
iOS Specific Best Practices:
Certificate Validation:
Certificate validation ko achi tarah se perform karo taaki insecure aur untrusted certificates ko accept na kiya jaaye.Secure Transport API Use Karna:
Jab client certificates ko designate kar rahe ho, Secure Transport API ka use karo.Self-Signed Certificates Avoid Karna:
Self-signed certificates ko avoid karo aur certificate pinning ko implement karo taaki app sirf trusted certificates ko accept kare.
Android Specific Best Practices:
Insecure SSL Code Ko Remove Karna:
Development cycle ke baad insecure SSL code (e.g., AllowAllHostnameVerifier) ko remove karo, jisse attacker easily fake certificates ke saath app ko hijack na kar sake.SSL Certificates Ko Correctly Validate Karna:
SSL certificates ko correctly validate karo aur untrusted certificates ko accept mat karo, taaki communication secure rahe.
Example Attack Scenarios:
Lack of Certificate Inspection:
- Scenario: App TLS handshake successfully establish karta hai, lekin server ke certificate ko inspect nahi karta.
- Risk: Yeh man-in-the-middle attack ka risk create karta hai, jisme attacker encrypted traffic ko intercept kar ke sensitive information steal kar sakta hai, bina kisi suspicion ke.
Weak Handshake Negotiation:
- Scenario: App weak cipher suite negotiate karta hai, jo insecure encryption provide karta hai.
- Risk: Weak encryption attacker ko data ko easily decrypt karne ka chance deta hai, jisse sensitive information ka exposure ho sakta hai.
Privacy Information Leakage:
- Scenario: App sensitive personally identifiable information (PII) ko non-secure channels ke through transmit karta hai.
- Risk: Jab sensitive data insecure channels (e.g., plain HTTP, SMS) ke through send hota hai, toh confidentiality compromise hoti hai aur attacker easily data intercept kar sakta hai.
Credential Information Leakage:
- Scenario: User credentials ko non-secure channels ke through transmit kiya jaata hai.
- Risk: Agar credentials non-secure channels (e.g., HTTP, open WiFi) se bheje jaate hain, toh attacker cleartext credentials ko intercept kar sakta hai aur unauthorized access gain kar sakta hai.
2FA Bypass:
- Scenario: Session identifier ko non-secure channels ke through receive kiya jaata hai, jisme encryption ya integrity checks nahi hoti.
- Risk: Yeh attacker ko two-factor authentication (2FA) bypass karne ka chance deta hai, jisme wo session hijacking ya brute-force attacks ke through 2FA ko sideline kar sakta hai.
Mitigation Suggestions:
- Proper Certificate Validation: Always validate server certificates to avoid man-in-the-middle attacks.
- Use Strong Cipher Suites: Ensure that only strong cipher suites are negotiated during the handshake to protect the encryption.
- Secure Transmission Channels: Always transmit sensitive data over secure channels like HTTPS and avoid non-secure options.
- Avoid Sending Credentials Over Insecure Channels: Ensure credentials are never sent over insecure channels, and implement secure storage practices.
- Protect Session Identifiers: Use encrypted and secure methods to transmit session tokens and 2FA codes to prevent bypass and session hijacking.
