🔍 𝗦𝗘𝗔𝗥𝗖𝗛 𝗘𝗡𝗚𝗜𝗡𝗘𝗦 𝗙𝗢𝗥 𝗣𝗘𝗡𝗧𝗘𝗦𝗧𝗘𝗥𝗦

🔍 Updated Search Engines for Pentesters
| # | Tool Name | Use Case | Explanation | Link |
|---|---|---|---|---|
| 1 | Shodan | Server | Internet se connected devices jaise camera, routers ki info search karne ka powerful tool hai. | shodan.io |
| 2 | Google Dorks | Dorks | Advanced Google queries se sensitive info nikalne ka tareeka. | google.com |
| 3 | Wigle | WiFi Networks | WiFi networks ki location aur details map karne ke liye. | wigle.net |
| 4 | Grep.app | Code Search | Publicly available code repositories (like GitHub) mein keyword search karne ke liye. | grep.app |
| 5 | BinaryEdge | Threat Intelligence | Exposed services aur assets ka global scan karta hai. | binaryedge.io |
| 6 | Onyphe | Server | Cyber threat intelligence + exposed hosts dikhata hai. | onyphe.io |
| 7 | GreyNoise | Threat Intelligence | Malicious traffic identify karta hai, attacker aur benign scanner mein difference batata hai. | greynoise.io |
| 8 | Censys | Server | SSL/TLS aur network devices ka large-scale scanning data provide karta hai. | censys.io |
| 9 | Hunter.io | Email Addresses | Kisi domain se associated email addresses find karne ke liye. | hunter.io |
| 10 | Fofa | Threat Intelligence | Shodan jaisa tool jo exposed devices aur services detect karta hai. | fofa.info |
| 11 | ZoomEye | Threat Intelligence | Internet-connected hosts ko fingerprint karta hai (Chinese version of Shodan). | zoomeye.org |
| 12 | LeakIX | Threat Intelligence | Open devices aur leaked info detect karta hai. | leakix.net |
| 13 | IntelX | OSINT | Public aur dark web info search karne ke liye, jaise email leaks, documents, etc. | intelx.io |
| 14 | Netlas | Attack Surface | Internet assets discover aur analyze karta hai (subdomains, ports, etc). | netlas.io |
| 15 | SearchCode | Code Search | Open source projects mein code search karne ka tool. | searchcode.com |
| 16 | UrlScan | Threat Intelligence | Website scan karta hai aur HTTP requests ka breakdown deta hai. | urlscan.io |
| 17 | PublicWWW | Code Search | Websites ke source code mein specific string/tech dhoondhne ke liye. | publicwww.com |
| 18 | FullHunt | Attack Surface | Real-time attack surface monitoring karta hai (great for recon). | fullhunt.io |
| 19 | SocRadar | Threat Intelligence | Threat monitoring, dark web tracking, aur brand protection ke liye. | socradar.io |
| 20 | IVRE | Server | Network recon aur passive scanning tool. | ivre.rocks |
| 21 | crt.sh | Certificate Search | SSL/TLS certificates ka public database — certificate transparency check karne ke liye. | crt.sh |
| 22 | Vulners | Vulnerabilities | CVEs aur software vulnerabilities ka search engine. | vulners.com |
| 23 | Pulsedive | Threat Intelligence | Threat intelligence indicators ko enrich aur correlate karta hai. | pulsedive.com |
| 24 | 🆕 DNSdumpster | Subdomain Enumeration | Kisi domain ke subdomains aur DNS records find karne ke liye. | dnsdumpster.com |
| 25 | 🆕 Spyse | Attack Surface / OSINT | Domain aur IP address se related deep OSINT data provide karta hai. | spyse.com |
| 26 | 🆕 ThreatCrowd | Threat Intelligence | Domain/IP/Hash ke basis pe malware aur threat info dhoondhne ke liye. | threatcrowd.org |
| 27 | 🆕 SecurityTrails | Attack Surface | Subdomains, DNS history, WHOIS info aur assets discovery ke liye. | securitytrails.com |
| 28 | 🆕 Certspotter | Certificate Search | Certificate transparency log search karne ke liye alternative tool. | sslmate.com |
| 29 | 🆕 AlienVault OTX | Threat Intelligence | Indicators of Compromise (IoC) aur community-shared threat data ke liye. | otx.alienvault.com |
| 30 | 🆕 GitHub Dorks | Code Search | Sensitive files like .env, API keys, etc. GitHub repositories se dhoondhne ke liye. | github.com |
What is Red Teaming?
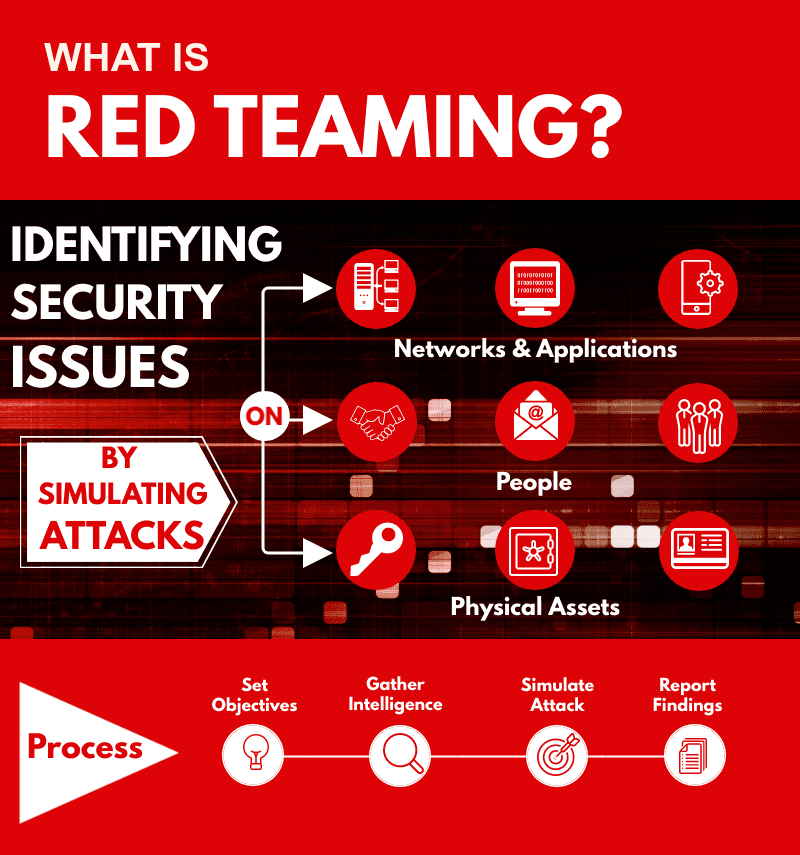
Red Teaming ek aisa simulation hota hai jo bilkul real attacker ke jaise conduct kiya jaata hai, aur yeh simulation har company ke liye uske specific risks ke hisaab se banaya jaata hai. Iska main purpose yeh hota hai ki ek independent security team real-world attack perform kare taki yeh dekha ja sake ki organization ke defense system mein kaha se breach ho sakta hai. Isse business ko apne security gaps ka pata chal jaata hai aur wo unhe fix kar sakta hai.
“Red Teaming” term ka origin military aur intelligence agencies se hua hai. Iska main concept yeh hai ki organization ki security ko ek attacker ki nazar se analyze kiya jaaye.
Red Team generally initial access credentials chura kar ya Social Engineering jaise techniques ke through leti hai. Network ke andar ghusne ke baad, wo apne privileges escalate karti hai aur lateral movement karke dusre systems tak pahuchti hai — taaki network ke core tak access mil sake, bina detect hue.
Red Teaming itna important kyun hota hai?
Red Teaming aapki company aur uske saare assets ko protect karne mein madad karta hai. Yeh sirf technology tak simit nahi hota — balki yeh aapke logon (employees), systems aur physical locations sabhi ko cover karta hai, taaki aap har possible threat ke liye tayyar rahein.
Chhoti ya badi, har size ki company ke liye Red Teaming zaroori hoti hai, kyunki Red Teaming traditional penetration testing se kaafi different hoti hai.
Red Teams generally zyada creative hoti hain, aur “out of the box sochti hain” — jiska matlab hai ki wo aise tareeke se attack karte hain jaise real attackers sochte hain, jo ek normal pentest shayad miss kar de.
The Red Team Methodology

Red Teaming ke Main Steps
Initial Reconnaissance (Pehli Jaankari Jama Karna):
Attacker sabse pehle apne victim ke baare mein research karta hai. Wo decide karta hai ki kisko target banana hai (chahe wo systems ho ya log), aur kis strategy se attack karega. Wo aise Internet-facing services ya logon ko dhoondta hai jinko exploit kiya ja sakta hai.Initial Compromise (Pehla Attack):
Attacker victim ke system par malicious code run karne mein successful ho jaata hai. Yeh usually social engineering, especially spear phishing, ya kisi vulnerable system ko exploit karke kiya jaata hai.Establish Foothold (Apna Control Banaana):
Jab attacker kisi system mein ghus jaata hai, toh wo ensure karta hai ki uska access bana rahe. Iske liye wo backdoor install karta hai ya koi malware download karke system par control bana leta hai.Privilege Escalation (Zyada Access Pana):
Ab attacker apne access ko aur powerful banata hai. Wo password hash dump karta hai, logs se credentials nikalta hai, privileged applications ka misuse karta hai ya kisi weak software ko exploit karke admin-level access tak pahuchta hai.Internal Reconnaissance (Andar Ka Jaayza Lena):
Attacker organization ke network ke andar ki jaankari collect karta hai — jaise ki kaun important hai, kaun kya kaam karta hai, aur sensitive information kahaan stored hai.Lateral Movement (Network Ke Andar Ghoomna):
Ab attacker ek system se dusre system mein move karta hai, taaki network ke core tak pahuch sake aur aur zyada systems ko control kar sake.Maintain Presence (Access Banaye Rakhna):
Attacker ensure karta hai ki uska access disturb na ho, aur wo future mein bhi system mein ghus sake. Iske liye wo persistence mechanisms use karta hai.Complete Mission (Apna Goal Achieve Karna):
End mein attacker apna main objective complete karta hai — jaise ki intellectual property, financial data, PII (Personally Identifiable Information) ya confidential company deals jaise mergers & acquisitions ki information chura lena.
💡 Red Teaming Kaise Kaam Karta Hai?
Red Team agar network ke andar ghusna chahti hai bina detect hue, toh unhe bahut clever aur deceptive banna padta hai — jaise ek real attacker hota hai. Ek ideal Red Team member kaafi technical bhi hota hai aur creative bhi, jise systems ke flaws aur insaano ki psychology ka faayda uthana aata hai.
Red Team ke members ko TTPs (Tactics, Techniques, and Procedures) ka accha knowledge hona chahiye — jaise jo methods real-world attackers use karte hain, unke tools aur frameworks.
🔧 Red Team Member ke Pass Kaun Kaun Si Skills Honi Chahiye?
💻 Systems aur Protocols ka Deep Knowledge:
Computer systems, protocols, security tools aur defensive techniques ka accha understanding.👨💻 Strong Programming Skills:
Custom tools banane ke liye programming skills honi chahiye jo traditional security tools ko bypass kar sakein.🛠️ Penetration Testing Experience:
Common vulnerabilities ko exploit karne ka experience, bina detect hue operate karna.🗣️ Social Engineering Skills:
Logo ko trust mein lekar unse credentials ya sensitive info nikalna aana chahiye.
🔄 Red Teaming Process (Steps of a Typical Exercise):
Stage | Explanation |
|---|---|
🎯 Objective Define Karna | Sabse pehle organization aur red team milkar decide karte hain ki test ka goal kya hoga — jaise ek specific server se sensitive data nikalna. |
🔍 Reconnaissance | Target environment ka full map banaya jaata hai — jaise ki network services, web apps, employees ki details wagairah. |
🎣 Initial Access | Phishing ya kisi vulnerability ka use karke target system par session banane ki koshish ki jaati hai. |
🕵️ Post Access Recon | Jab access mil jaata hai, toh red team further explore karti hai ki aur kaha se attack kiya ja sakta hai. |
🚀 Privilege Escalation | Zyada access paane ke liye vulnerabilities ka use kiya jaata hai — jaise admin ya root privileges lena. |
🎯 Target Access | Jab required access mil jaata hai, toh final goal achieve kiya jaata hai — jaise sensitive data ya asset ko access karna. |
Asal mein, ek experienced Red Team member har phase ko complete karne ke liye bahut saare different methods use karta hai. Lekin jo main conclusion hai upar diye gaye sample attack scheme se, wo yeh hai ki — chhoti-chhoti vulnerabilities agar alag-alag systems mein ho, toh jab unhe chain ki tarah joda jaata hai, toh wo ek badi security failure ban sakti hain

Red Team ke saath Exercise karna
Red team security architecture ke flaws ka faayda uthane ke liye alag-alag approaches aur tools ka use karti hai. Ek red team ka member, for example, malware ka use karke host ko infect kar sakta hai jisse security protections disable ho jayein, ya phir hacker ban kar social engineering tactics ke through access credentials le sakta hai.
MITRE ATT&CK Framework, jo ek globally available knowledge base hai real-world tactics, techniques, aur methodologies ka, red team events mein aksar use hota hai. Ye framework ek platform provide karta hai jo prevention, detection, aur response capabilities develop karne mein madad karta hai, aur ye organization ki specific needs aur naye threats ke according customize kiya ja sakta hai. Saath hi, red teams Cyber Kill Chain pattern ko bhi follow karke apne attacks design karti hain.
Yahan kuch red team activities ke examples diye gaye hain:
Penetration testing: Jab red team ka member real-world tactics ka use karke system me access lene ki koshish karta hai.
Social engineering techniques: Employees ya network members ko manipulate karke unse network credentials lena, disclose karwana, ya jhootay credentials banana.
Communication intercept karna: Network ka map banane ke liye ya surroundings ke baare me zyada jaanne ke liye jisse standard security measures ko bypass kiya ja sake.
Administrator ke access cards clone karna: Un locations me access paane ke liye jo normally prohibited hoti hain.
MITRE ATT&CK Framework kya hai?
2013 me, MITRE ne MITRE ATT&CK Framework publish kiya tha jo attackers ke tactics aur approaches ko real-world observations ke basis par detail karta hai. Yeh ek continuously updated index hai jo naye threats aur attack techniques ko include karta rehta hai, taaki threat landscape ke changes ko reflect kiya ja sake.
Aaj ke time me, yeh framework cybersecurity industry ka ek well-known information repository ban chuka hai. Yeh organizations aur security professionals ko attackers ke models, techniques, aur countermeasures ko better understand karne me madad karta hai.
Cyber Kill Chain Method kya hai?
Cyber Kill Chain ek cybersecurity model hai jo Lockheed Martin ne banaya tha. Iska main purpose hai ek cyber-attack ke different stages ko trace karna, unme hone wali vulnerabilities ko identify karna, aur security teams ko har stage par attack ko detect aur stop karne me madad karna.
Yeh model attackers ke step-by-step process ko samajhne ke liye use hota hai, jisse defenders unhe early stage me hi rok sakein.
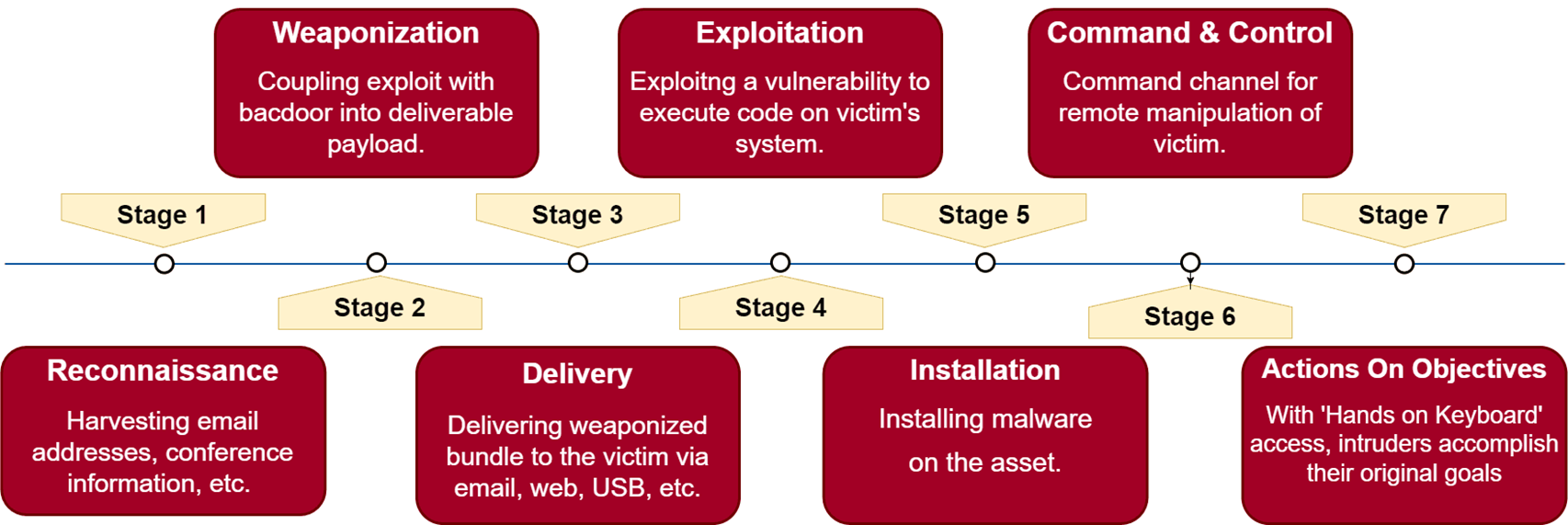
Cyber Kill Chain ke main stages kuch is tarah hoti hain:
Reconnaissance – Target ki information gather karna
Weaponization – Malware ya exploit create karna
Delivery – Malware ko target tak pahunchana (jaise email, USB, etc.)
Exploitation – Malware ka target system par run hona
Installation – Malware ka system me install ho jana
Command and Control (C2) – Remote access ke liye attacker ka system se connect hona
Actions on Objectives – Final goal achieve karna (jaise data theft, destruction, etc.)
Yeh method red teamers aur defenders dono ke liye kaafi useful hota hai to visualize, understand aur disrupt karne ke liye attacker ka path.
Example Red Teaming Scenario
Ek example scenario dikhaya gaya hai jisme Cyber Kill Chain method ka use kiya gaya hai:

| Stage | Scenario |
|---|---|
| 🔍 Reconnaissance | Customer ke IP addresses, un IPs par open ports, ports par chalne wale services, employees ke social media aur email addresses ko identify kiya jaata hai. |
| 💣 Weaponization | Exploit code ya malware banaya jaata hai aur USB device ke andar install kiya jaata hai. |
| 📤 Delivery | Jahan log active hote hain, us jagah prepared USB device gira diya jaata hai. Logon ki curiosity ka faayda uthakar ensure kiya jaata hai ki koi us USB ko utha le. |
| 💻 Exploitation | Jo vyakti USB device uthata hai, jab wo usse customer ke computer me lagata hai toh target computer ka access mil jaata hai. |
| 🔧 Installation | Target computer par user ki authorization control check ki jaati hai. Agar low-privilege user hai toh privilege escalate kiya jaata hai. Agar already high privilege hai, toh registry key "HKCU\Software\Microsoft\CurrentVersion\Run" ke through persistence banayi jaati hai. Baad me logged-in users ke passwords memory se extract kiye jaate hain. |
| 🌐 Command & Control | Command server se communication establish kiya jaata hai. “Pass the Hash” attack se horizontal movement ki jaati hai. Jab tak Domain Admin ka access nahi milta, tab tak har logged-in user ki memory se unka session data nikala jaata hai. |
| 🎯 Actions on Objectives | DNS Tunneling, SSH Tunneling, ya ICMP Tunneling jaise methods ka use karke organization ka sensitive data leak kiya jaata hai. Red Teaming tab tak chalu rehta hai jab tak required data extract nahi ho jaata. |
Pentest ek aisi activity hoti hai jo participants ke knowledge ke saath ki jaati hai. Ye stealthy ya chupke se nahi hoti, aur ismein Blue Team ke paas detect aur respond karne ki capability nahi hoti, kyunki Blue Team ko pehle se scope aur test ke baare mein pata hota hai.
Red teaming, doosri taraf, un advanced threat actors par focus karta hai jo stealth ka use karke real-world attacks karte hain. Iska main purpose hota hai defensive approach mein weaknesses identify karna. Kisi organization ka real-world attacks ke response ko samajhna hi iski asli value hai.
Kyuki red teaming ek covert operation hota hai, ye Blue Team ke bina bataye kiya jaata hai. Agar Blue Team kisi malicious activity ko detect kar leti hai, to wo turant action leti hai.

| Penetration Testing | Red Team Assessments |
|---|---|
| Main goal hota hai jitni zyada vulnerabilities dhoondhna ek limited time frame mein. | Har assessment individually design hota hai taaki business ke liye ek important contribution dikhaya ja sake, open-scope objective ke saath. |
| Saare business stakeholders, jaise ki Development aur IT Operations ko inform kiya jaata hai. | Sirf Exercise Working Group ko hi pata hota hai ki exercise ho rahi hai. |
| Implementation industry-recognized technical approaches follow karta hai, jaise OWASP. | Real-world enemies ke Tactics, Techniques, aur Procedures (TTPs) ko imitate kiya jaata hai execution mein. |
| Social engineering aur physical security jaise attacks normally cover nahi hote. | Exercise Working Group ki permission ke saath, social engineering aur physical security attacks bhi kiye ja sakte hain. |
